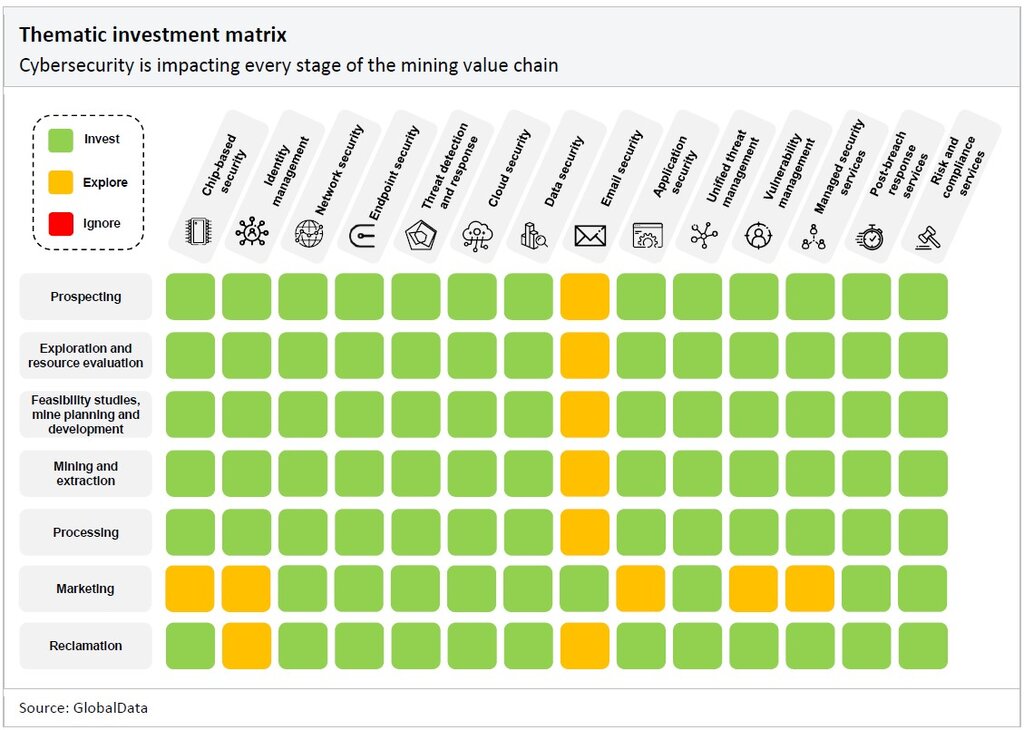
The number of cyberattacks is rising, and so is their complexity. Therefore, all segments of the mining value chain are vulnerable to attack. The matrix below details the areas of cybersecurity in which mining companies should focus their time and resources. Mining companies should invest in technologies shaded green, explore the prospect of investing in technologies shaded yellow, and ignore technologies shaded red.
How mining should invest in cybersecurity
With IoT devices rapidly increasing in popularity and deployment, attackers are shifting their attention to the vulnerabilities of digital integrated circuits (ICs). Therefore, mining companies should invest in chip-based security.
Regarding the software segment of the cybersecurity value chain, mining companies will need to use all cybersecurity software provisions, from identity management to vulnerability management, to defend servers and IoT devices collecting data. For example, at the prospecting and exploration stages, there is the risk of theft of important geological data, surveys, and mapping of economically valuable mineral deposits. Mining companies invest billions of dollars into identifying new mine sites, and data on mineral deposits can be sold to competitors.
Moreover, during the extraction and processing stage, threats involve unauthorized access to automated equipment, affecting production activity and worker safety. With the increasing reliance on mobile and remote access technologies, ensuring the security of endpoints such as laptops, tablets, and mobile phones is vital since geologists and engineers often work in remote locations and use mobile devices to collect and analyze data. Endpoint security solutions protect these devices from malware and unauthorized access.
Mining companies increasingly rely on cloud services for data storage, analytics, and collaboration. A breach could expose large-scale project data, including blueprints and timelines, leading to delays and financial losses. Therefore, mining companies should invest in robust cloud security measures.
Unauthorized access to networks could lead to operational disruptions. By investing in network security and deploying measures such as intrusion detection systems (IDS) and secure communication protocols, mining companies can safeguard their networks against cyber threats.
Threat detection and response (TDR) and unified threat management (UTM) are other priorities across all mining value chain segments. Where these applications are AI-based, they can be useful in preventing cyberattacks and monitoring all threats despite mining operations being spread worldwide.
Cybersecurity services are a high priority since they offer expert support for complex cybersecurity issues in an industry with a shortage of cybersecurity skills.
How does ESG impact cybersecurity?
ESG considerations drive the need for cybersecurity within the mining sector. By addressing cyber risks within the context of sustainability, social responsibility, and effective governance, companies can safeguard their operations, customers, and reputation while fulfilling their ESG responsibilities. By protecting themselves from cyber threats, mining companies align with ESG objectives.
The mining industry increasingly relies on digital technologies to improve efficiency and sustainability. Cyberattacks on critical infrastructure, such as power plants and water-processing facilities, pose environmental hazards. Again, disruptions to the decarbonization and CO2 reduction database or the monitoring system of energy production and consumption are an opportunity for cybercrime.
Cybersecurity is integral to trustworthy ESG reporting, protecting data from collection to analysis and reporting. It is worth mentioning, however, that implementing cybersecurity measures (i.e., having a backup data center) can lead to higher resource and energy consumption.
Mining companies are under growing pressure to demonstrate social responsibility by safeguarding the interests of employees, local communities, and stakeholders. Social harms - such as breaches targeting personal employee data and financial frauds like breaches in production scheduling and pricing information - pose significant threats. Privacy controls play a crucial role in limiting the manipulation of personal data.
Risk management, transparency, and accountability are part of the governance component of the ESG framework for the mining sector. Integrating cybersecurity into governance frameworks (e.g., appointing a CISO to the board) ensures that cybersecurity receives appropriate attention and resources.
How does safety impact cybersecurity?
Safety in mining operations involves protecting workers from harm, equipment problems, and environmental dangers. However, the increasing reliance on digital technologies and interconnected systems introduces cybersecurity risks that can compromise safety.
For instance, if hackers attack the control systems of mining equipment, it could cause malfunctions or accidents, putting workers at risk. Moreover, standby systems are critical for processes such as furnace cooling or mine ventilation, and a potential cyberattack represents a significant hazard.
Electronic control systems are a fundamental safety feature. Examples include remote control systems that manage haul trucks, fire detection and suppression systems, and tailing impoundments. If a control breach occurs, the malfunction of electronic monitoring and warning systems can compromise the safety of thousands of workers. Also, if sensitive safety or environmental monitoring data gets breached, it can affect compliance with regulations and create safety problems in the long run.
How does geopolitics and supply chain risk impact cybersecurity?
Mining companies face cybersecurity threats from various actors who may target them to weaken a country or industry. For instance, a cyberattack aimed at stealing pricing data could give competitors or foreign countries an advantage in future sales. Factors such as geopolitics, volatile market dynamics, and regulatory changes add further pressure to the sector, creating an environment where cyber threats proliferate.
The mineral supply chain is vulnerable to political interference, with state-sponsored threats seeking to disrupt operations and steal valuable mining data, including exploration information, geological surveys, and financial data. The geopolitical landscape, shaped by events like the conflict in Ukraine, tensions in the Middle East, Red Sea attacks, and deteriorating Western relations with China, directly affects cyber threats.
State-sponsored attacks on critical infrastructure and supply chains are increasingly sophisticated and aggressive. Implementing preventive measures (i.e., encryptions, authentications, backup systems, training, etc.) and collaborating with cybersecurity vendors strengthens cyber resilience.
How does productivity impact cybersecurity?
More digitalization is needed to increase productivity in mining operations. However, the reliance on digital systems and devices brings more cybersecurity risks.
Automation plays a crucial role in building productive and resilient businesses, so the mining sector is looking at emerging technology to address labor shortages, cut costs, and ease the negative consequences of supply chain disruption. This includes technologies that replace human labor, such as robotics, or technologies that help workers collaborate remotely, such as digital twins, wearable tech, and virtual and augmented reality (VR and AR).
Additionally, IoT sensors, autonomous vehicles, and drones are becoming integral parts of industrial automation strategies within the sector. However, industrial automation brings challenges. Although beneficial for productivity, it increases the risk of cyberattacks, a worrying issue for mining companies.
With larger volumes of data being generated and processed, including sensitive information about production processes and equipment, safeguarding this data becomes crucial to prevent disruptions and ensure safety. Therefore, maintaining security measures is essential to protect mining operations.
How does the labor shortage impact cybersecurity?
The labor shortage in the mining sector is making it harder to protect companies from cyber threats. With fewer skilled workers available, there is less expertise to implement cybersecurity measures, leading to vulnerabilities. The workload on current staff increases, causing delays in spotting and addressing cyber threats.
Human error remains a leading cause of breaches, but building awareness, providing updated information to the staff, and enhancing password security can help prevent data leaks. Mining companies must prioritize cybersecurity investments to increase their cybersecurity expertise, resources, and responsiveness to threats. For instance, they should hire new talent with cybersecurity expertise and focus on upskilling existing employees.
How does resource development impact cybersecurity?
As mining operations look into more challenging environments and explore new frontiers like deep-sea and extra-terrestrial exploration, the increased reliance on digitalization and connectivity increases the potential for cyber threats. Moreover, exploring and developing new mines in remote or difficult-to-access locations requires complex supply chains involving various vendors, contractors, and partners. This complexity introduces vulnerabilities within the supply chain, increasing exposure to cyber risks.
GlobalData, the leading provider of industry intelligence, provided the underlying data, research, and analysis used to produce this article.
GlobalData’s Thematic Intelligence uses proprietary data, research, and analysis to provide a forward-looking perspective on the key themes that will shape the future of the world’s largest industries and the organisations within them.